Oracle Service Bus (OSB) 12c LDAP Authorization – HTTP 401 (Unauthorized)
Oracle Service Bus 12.2 and onwards is available to download on Oracle Support. As you might expect, the new version brings some changes for middleware admins and new features to developers when configuring an installation from scratch.
Among them, on the OSB 12c version, user privileges and group roles are managed via the EM (Enterprise Manager) Console. This can make things a little confusing when deploying Oracle Service Bus (OSB) architecture.
I experienced a small inconvenience the first time I tried to use OSB with LDAP (Lightweight Directory Access Protocol) authorization, so I documented the issue here for you.
My issue: after configuring the authentication of Weblogic in LDAP, I was able to log in to the Weblogic Console (/console). However, I was unable to log in to Service Bus Console and received error HTTP 401 (Unauthorized).
In WL Admin log ($DOMAIN_HOME/servers/AdminServer/logs/*.???) I found the following:
[AdminServer] [ERROR] [ADFC-50017] [oracle.adfinternal.controller.application.AdfcExceptionHandler] [tid: [ACTIVE].ExecuteThread: '20' for queue: 'weblogic.kernel.Default (self-tuning)'] [userId: LDAP_ACCOUNT ] [ecid: fdf185a3-35fd-4171-9b75-4b80a0f40b03-000000cf,0] [APP: service-bus] [partition-name: DOMAIN] [tenant-name: GLOBAL] [DSID: 0000Lu77u7K7q2r6wJAhMG1Pj34E000001] ADFc: While attempting to handle this exception the application's exception handler failed.[[ oracle.adf.controller.security.AuthorizationException: ADFC-0619: Authorization check failed: User 'LDAP_ACCOUNT' does not have 'VIEW' permission on 'jsf.resourcesPageDef'.
Error 401–Unauthorized
From RFC 2068 Hypertext Transfer Protocol — HTTP/1.1:
10.4.2 401 Unauthorized.
Here’s the workaround:
For OSB 12c Console, you need to use Enterprise Manager (/em) to add your LDAP user (or a group that they’re a member of) to an “application role” for the Service_Bus_Console application. The monitor application role is the basic role that allows OSB Console access.
Example: To use the Enterprise Manager add a user or group to the monitor application role for Service_Bus_Console:
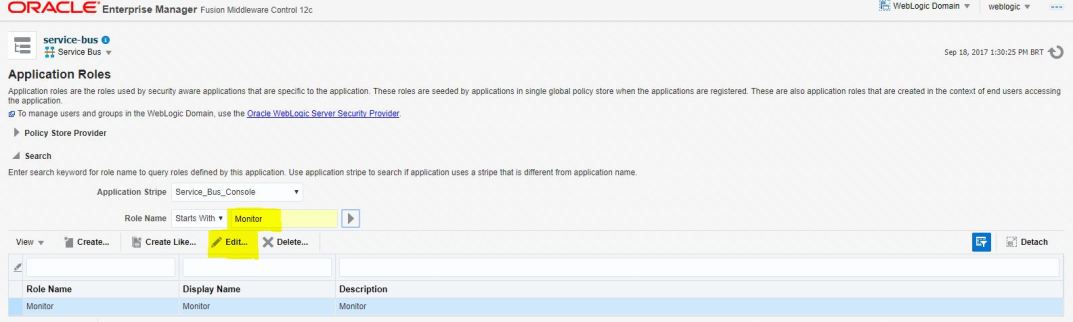
1. Go to Enterprise Manager Console -> SOA -> service-bus -> (right click) -> Security -> Application Roles

2. Search for Role Name
Application Stripe: Service_Bus_Console
Role Name (Starts With): Monitor
3. Select the monitor role, and choose Edit -> Add
A new screen will appear to add the role.
4. Select the type as either user or group, depending on who you want to give the monitor role to.
5. You can now try searching for your user or group here (enter a user or group name for the principal name and click search).
One caveat: it seems that if the user / group only exists in LDAP, the search in this screen may not find them.
To work around this, after you choose “user” or “group” as the type (in step 3), you should see an “advanced option” appear at the bottom of the screen. If you select this advanced option checkbox, it allows you to manually type in your LDAP user or group name.
Once your user or group is a member of the monitor application role for Service_Bus_Console, they should be able to access the OSB Console.
I hope this was helpful. Please feel free to ask any questions or leave feedback in the comments.
Share this
Share this
More resources
Learn more about Pythian by reading the following blogs and articles.
How to Use EM CLI to Verify Data Guard Configurations

A Quick-and-Easy Solution for the Oracle Enterprise Manager (OEM) Unique Domain Identifier Error

Part Three: Deploying High Available Applications in Oracle Cloud Infrastructure – Instance Clone and Linux Storage Appliance
Ready to unlock value from your data?
With Pythian, you can accomplish your data transformation goals and more.
